This article highlights some of the more frequently asked questions for Security-related topics in Productiv.
Let's get started!
- What is Shadow IT?
- What is SOC 2 compliance?
- What is Single Sign On?
- What is a Service Account?
- What are standard SSO protocols?
- What is SCIM?
- What is the importance of the SMTP Server and DKIM setting?
FAQs
Q: What is Shadow IT?
A: This refers to software and tools that are set up by departments that are not a centralized IT organization. This leads to concerns regarding security, spend, access, reliability, etc. However, it's also worth noting that Shadow IT can be an important source of innovation and information for the IT team.
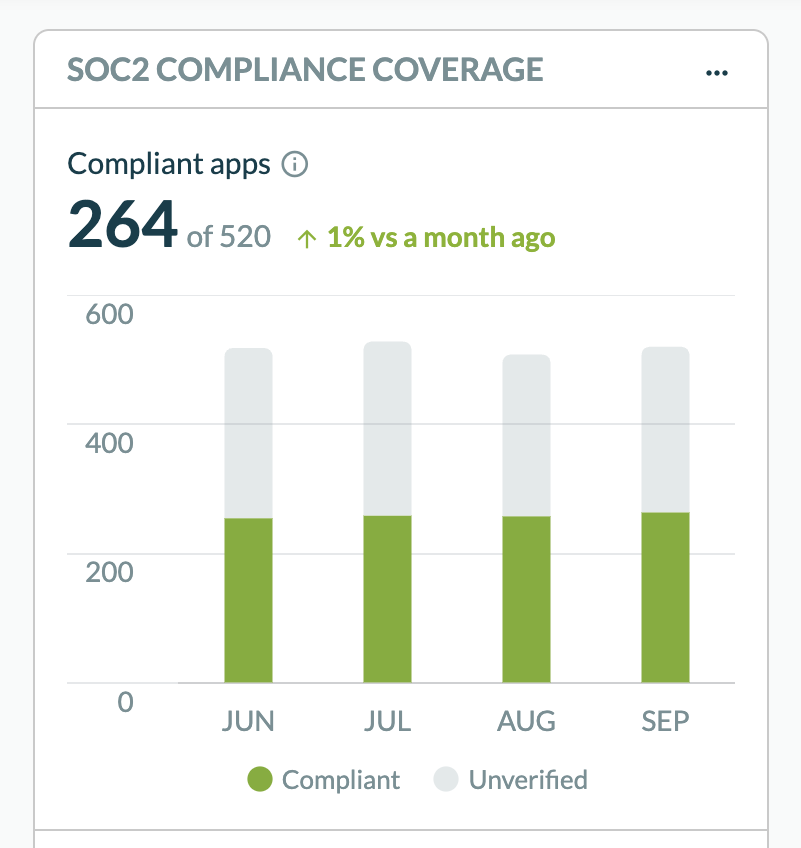
Q: What is SOC 2 compliance?
A: Compliance with SOC 2 is considered tablestakes when IT teams evaluate software products. SOC 2 compliance defines criteria for managing customer data based on 5 trust service principles: security, availability, processing integrity, confidentiality, and privacy. SOC 2 certification is done by outside auditors.
There are 2 types of SOC reports -- type I and type II. Type 1 describes a vendor's systems and whether their design is suitable to meet trust principles. Type II describes the operational effectiveness of those systems.
Q: What is Single Sign On?
A: Single Sign On (SSO) provides identity and access management. It allows customers to track user login activity. Examples include such platforms as Okta, Azure Active Directory, Duo Security, Idaptive, Jumpcloud, OneLogin, PingOne, and Google Workspace SSO.
Q: What is a Service Account?
A: This type of account is often used for authorization access to a vendor account when connecting to Productiv API integrations.
It typically is not tied to a particular employee, but to a general account such as ITAdminAccount@acme.co.
Using this type of account allows for independence between the employee who authorizes the app and Productiv’s access. This is a preferable option since people move on, change passwords, etc.
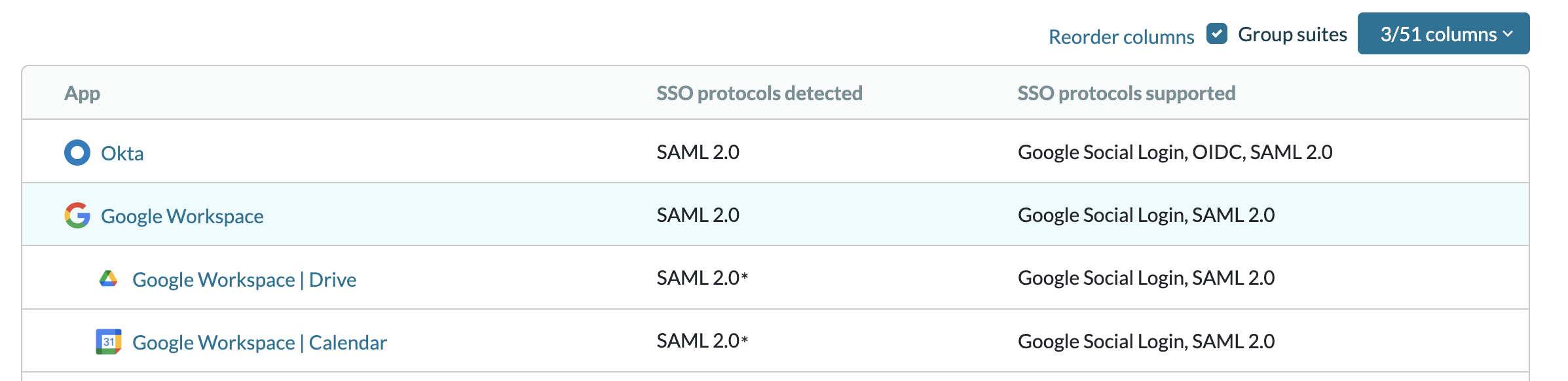
Q: What are standard SSO protocols?
A: These protocols are used to identify users during the SSO process. i.e. SAML and OIDC.
Q: What is SCIM?
A: System for Cross-domain Identity Management (SCIM) is a standard for automating the exchange of user identity information between identity domains, or IT systems. It specifically helps automatically create app profiles, allows the exchange of user information, and is also used to delete user profiles.
For apps that don't have SCIM, an admin has to manually create and manage an account for a user. i.e. Sigma doesn't support SCIM.
Q: What is the importance of the SMTP Server and DKIM setting?
A: We recommend setting up one of these (not both) to avoid Productiv notifications
from being sent to the spam folder.
SMTP effectively whitelists emails whereas DKIM effectively spoofs the Inbox by using a domain as the ‘From’ address in notifications.
Comments
0 comments
Please sign in to leave a comment.